In recent years, mobile gaming has surged in popularity, with a large number of games on the market facing varying degrees of security issues. These include common Cheats such as memory modification, auto click, and injection, as well as more severe forms of Hack and cheating.
Hack refers to the process by which cheaters create tools to bypass a game's signature verification, reverse-engineer and debug its internal code logic, modify game values and logic, and implant feature menus, thereby producing a hacked version of the game.
Common reverse engineering tools used during the hack process, such as MT Manager, allow access to system directories after obtaining root privileges. They enable mounting file systems for read/write operations and modifying file permissions and ownership. Key features include: bypassing signature verification, APK editing, DEX editing, XML editing, APK signing, and RES resource deobfuscation.
After bypassing signature verification, Hackers use reverse engineering tools to decompile the game's code logic. They then tamper with values and logic to implement various Cheats, while also implanting menu modules for easier operation.
Finally, hack developers attempt to repackage the hack game files. They combine the officially signed package with the hack version. When the game performs signature verification at launch, it detects the official signature, but during gameplay, it executes the hack package's content.
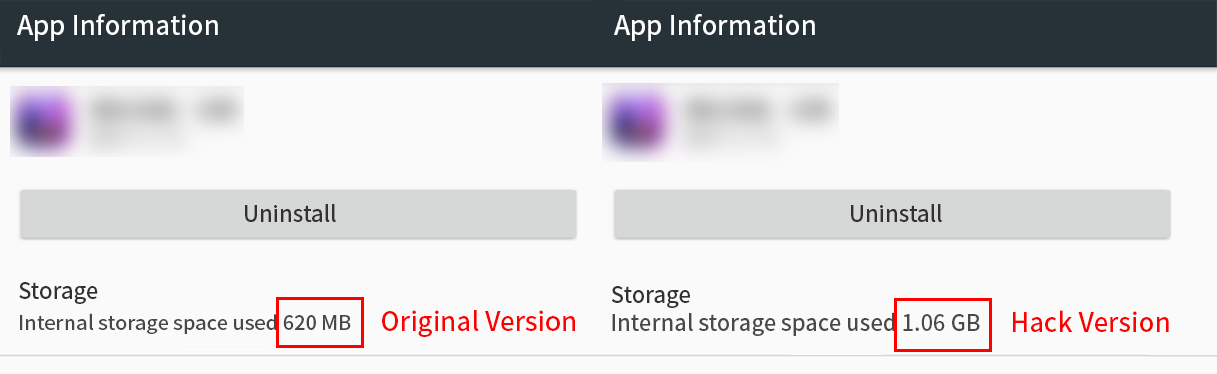
This is often reflected in the package size, with Hack versions being nearly twice as large as their legitimate counterparts.
Furthermore, game hacking implies that the game's code and resources have been fully reverse-engineered, potentially leading to operational incidents caused by resource leaks. There is also the risk of plagiarism by competing products.

To address the risk of game Hack, JikGuard has developed a specialized countermeasure strategy. This solution has been integrated into multiple popular games and has demonstrated outstanding protection capabilities.
Anti-Hack Features
JikGuard's industry-exclusive “API Signature Verification-Free Technology” employs deep encryption on game engines and code, coupled with multi-layered verification of game package signatures and file integrity. This significantly reduces the possibility of bypassing security measures, preventing malicious modules from being implanted into games or advertisements from being stripped out.
Proactive Malicious Module Detection Mechanism
Unlike other security products on the market that require obtaining samples before combating cheats, JikGuard's exclusive “Proactive Malicious Module Detection Mechanism” actively identifies suspicious modules within games. Combined with its online countermeasure capabilities, this enables proactive defense, significantly reducing the time required to investigate and eliminate cheats.
Anti-Debugging Feature
Prevents Cheats authors from debugging the game and blocks static or dynamic analysis. Upon detection, the game will immediately crash.
Security Environment Detection Capabilities
Unlike other products on the market, JikGuard employs deeper-level detection methods to accurately identify various risk environments such as virtual frameworks, virtual machines, jailbreaks, root access, and cloud phones, while providing customized crash prevention strategies.
Resource Encryption Feature
JikGuard's exclusive resource encryption solution is deeply integrated into the game engine's core architecture, meticulously designed to align with game resource file structures and loading mechanisms. It delivers robust encryption protection for games, featuring high compatibility, minimal runtime overhead, and no performance impact. The solution supports multi-platform deployment across Android, iOS, and PC, along with online resource updates. Additionally, it incorporates specialized optimizations that eliminate the need for developer integration or implementation, making encryption/decryption transparent to developers.