Game Hacking Case Analysis
Due to their lack of or weak connection to the internet, single-player games often encounter hacking problems. In addition, some games have also experienced serious archive sales, where paid players' archives/memory-tampered archives are sold to other players at extremely low prices, which seriously affects players' willingness to pay.
Game hacking is rampant
In addition to hacking, cheaters can also "modify memory" for character attack/health/defence and other numerical modules in the game. After modifying the memory, they can achieve features such as multiple attack, instant kill, acceleration and deceleration, etc., which reduce the difficulty of the game.
For stand-alone games, pirated versions and the sale of archives will quickly take over the space of genuine versions, destroy the balance of the game, and have a serious impact on the direct revenue of the game.
Case study of game resource leaks
The current game market is highly competitive in terms of art design. The quality of a game's art is a key factor in whether players choose to purchase it. In this context, encrypting and protecting game resources such as art concept art, scenes, character illustrations, and models to prevent unpacking leaks and resource theft is essential.
Halo 4 experienced an art asset plagiarism incident (Halo 4 above; Stellaris below)
For a game, the images, videos, and code in the game are all intellectual property. If they are hacked by hackers or competitors, competing products will be quickly copied, causing immeasurable impact and losses to the game.
JikGuard has customised a special response strategy for single-player games encountering problems such as hacking and resource leaks. This solution has been integrated into many popular games and has proven its excellent protection capabilities.
Anti-hack features
JikGuard uses its exclusive "API-free signature verification technology" to encrypt the game engine and code from the low-level, performing multiple verifications on game package signatures and file integrity to prevent malicious modules from being implanted into the game.Anti-memory modification features
In response to the risk of memory modification faced by games, JikGuard has devoted itself to the research and development of a "behaviour detection solution". Through a sensitive intelligent perception system, once a modification is detected, it can immediately crush the game, detect various types of modification cheats and their variants, and provide effective protection.Resource encryption features
JikGuard's exclusive resource encryption solution goes deep into the low-level game engine and is carefully constructed in combination with the game resource file structure and loading mechanism.It provides high-strength encryption protection for games, with high compatibility, low running consumption, and no impact on performance. It supports Android/iOS/PC platforms and online resource updates. In addition, the solution has been specially optimised, eliminating the need for development docking and access, and making encryption and decryption transparent to developers.
Archive encryption recommendations
Due to differences in game development processes, there is no one-size-fits-all solution for archive encryption. JikGuard offers the following recommendations:Save file encryption should use keys related to the device ID to prevent save files from being copied to other devices for reading.
It is recommended that games store save files in the internal storage directory. Using the SD card as the save file directory carries the risk that save files can be read, written, or modified by other applications.
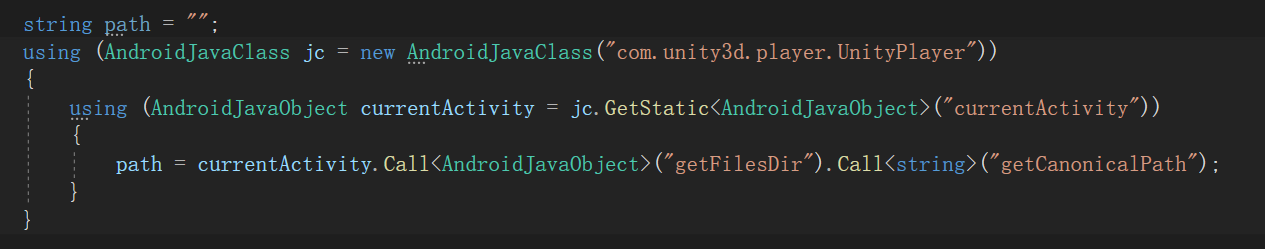
Here is a relatively simple method to obtain the internal storage path, as shown in the code below:
- How to Anti Hack in Client-Side Games








