Initial access broker services are a booming dark web market, with threat actors able to purchase a variety of options at low cost, according to a new Rapid7 report.
Over a third (39%) of sales of these services, which provide customers with access to already compromised networks, are grouped in the $500-$1000 price range.
The average base price of a sale across all three cybercrime forums analyzed by Rapid7 was just over $2700. The researchers analyzed three prominent sites over a six-month period from July 1 to December 31, 2024 – Exploit, XSS and BreachForums.
The brokers were observed using the victim organization’s revenue to help justify the value of the asking price.
Read now: Initial Access Brokers Target $2bn Revenue Companies
Around three-quarters (71.4%) of brokers offered a variety of options with each sale, such as a choice of more than one entry point into the compromised organization, or in nearly 10% of cases, a bundle that includes multiple initial access vectors (IAVs) and/or privileges.
The remaining 17.5% of brokers only offered a single form of access with no privilege included.
The researchers said the findings demonstrate that the initial access broker services have become both inexpensive and easy to obtain for threat actors of any skill level.
“The heavy lifting has been addressed by the access broker; all the willing buyer has to do is pay a few hundred dollars to gain immediate access to an already compromised business,” the researchers wrote in the report dated August 12.
Account Compromise the Most Common Type of Access
The Rapid7 report found that compromised accounts were the most frequent initial access vector on offer across packages.
VPN accounts led the way, appearing in 23.5% of sales across all three forums. This was followed by domain user accounts (19.9%), remote desktop protocol (16.7%) and domain admin accounts (5.5%).
Attackers using VPN accounts purchased from an initial access broker is an effective way of avoiding detection in networks, as they come equipped with valid credentials, enabling them to blend in with expected VPN traffic.
“These combinations of VPN, RDP, and domain/admin user accounts can enable all manner of network exploration, lateral movement, and further escalation into ransomware delivery and data exfiltration,” the researchers commented.
BreachForums Resurfaces in Late July
One of the analyzed cybercrime forums, BreachForums, has been subject to multiple law enforcement actions in recent years, including takedowns and arrests of individuals alleged to be involved in running the site.
This includes the FBI’s arrest of Conor Brian Fitzpatrick, also known as 'Pompompurin', in March 2023. Fitzpatrick was suspected of being the main administrator of the platform, which temporarily ceased its activities, but came back online, supposedly with a new administrative team.
On June 25, 2025, the US charged a British national, Kai West, with offenses related to his alleged involvement in operating the platform. Kai was arrested in February 2025.
Around April 15, the BreachForums site went offline and there was much speculation surrounding the event that could have triggered the outage.
The site and did not officially resurface until July 25 when the administrator posted a defiant message declaring “it’s business as usual.”
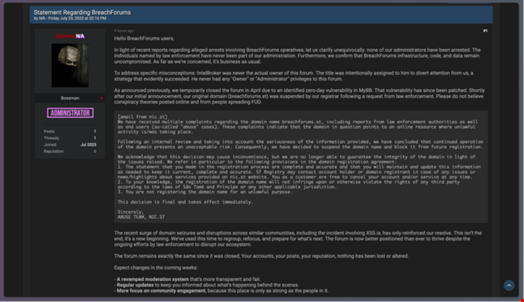 BreachForums message on July 25 announcing “business as usual.” Source: Rapid7
BreachForums message on July 25 announcing “business as usual.” Source: Rapid7
The most prolific poster to BreachForums in the six-month period analyzed was IntelBroker, the pseudonym used by West. This account made up 19.05% of all sales over the period.
No tags.