The global average cost of a data breach fell by 9% to $4.44m in 2025, the first decline observed in five years, according to IBM’s Cost of a Data Breach Report 2025.
The fall has been attributed to improved detection and containment capabilities in organizations, boosted by AI and automation tools.
The researchers found that average costs for detection and escalation fell to $1.47m, representing a nearly 10% drop compared to 2024.
The mean time organizations took to identify and contain a breach fell to 241 days, a nine-year low and continuing a downward trend since 2021.
Organizations using AI and automation extensively throughout their security operations saved an average $1.9m in breach costs and reduced the breach lifecycle by an average of 80 days, according to the study, published on July 30.
“Globally, shorter breach investigations are pushing down detection and escalation costs, which can include assessment and audits, crisis management, and communications to executive leadership and boards,” read the report.
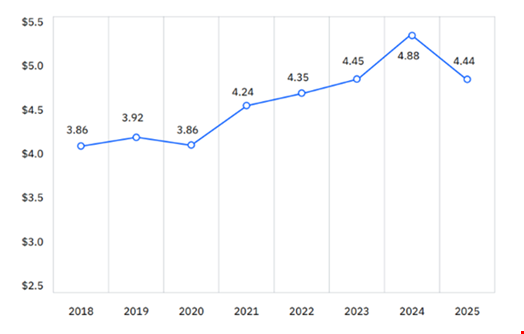 Average global cost of a data breach, 2018-2025 in USD. Source: IBM
Average global cost of a data breach, 2018-2025 in USD. Source: IBM
In contrast to the global trend, the average breach costs in the US reached $10.2m, a 9% increase over the past year.
The researchers said this rise is largely due to higher regulatory fines and increased detection and escalation costs in the region.
The industry that recorded the highest average breach cost was healthcare, at $7.42m. This represented a significant decline from 2024, when the average cost was $9.77m.
This average cost was significantly higher than the next highest industry, financial, at $5.56m.
Healthcare breaches also took the longest to identify and contain, at 279 days. This was more than five weeks longer than the global average.
Attackers Focus on Customer Personal Data
The IBM report found that customer personally identifiable information (PII) was the most stolen or compromised data type, occurring in 53% of breaches.
PII includes tax identity numbers, emails and home addresses, and can be used in identity theft and credit card fraud.
Employee PII was stolen or compromised in 37% of incidents, followed by intellectual property (33%) and non PII anonymized customer data (28%).
Other types of corporate data were compromised in 34% of cases.
Read now: Over 16.8 Billion Records Exposed as Data Breaches Increase 6%
Breached intellectual property data was the costliest for victim organizations, at $178 per record.
Around a third (30%) of all breaches involved data distributed across multiple environments, such as public clouds, private clouds and on premises.
Breaches involving data only stored on-premises increased significantly to 28% from 20% in the previous year.
Breached data stored across multiple environments took significantly longer to identify and contain, at 276 days, compared to data stored in single environments.
On-premises breaches were the quickest to resolve, at 217 days.
Phishing was the most common initial vector used by attackers to gain access to systems, making up 16% of breaches.
This was followed by vendor and supply chain compromise (15%), denial-of-service (12.5%) and compromised credentials (10%).
Breaches caused by third-party vendor and supply chain compromise took the longest to resolve on average, at 267 days.
This was followed by malicious insiders, at 260 days.
Breaches Involving AI Applications Grow
IBM found that 13% of organizations reported a security incident involving an AI model or application that resulted in a breach.
The majority (60%) of AI-related security incidents led to compromised data and 31% resulted in operational disruption.
Of those who suffered such breaches, 97% admitted that they lacked proper AI access controls.
Read now: OWASP Launches Agentic AI Security Guidance
Supply chain compromise was the most common cause of security incidents involving AI tools, at 30%. This includes compromised apps, APIs and plug-ins.
Following supply chain compromise were model inversions (24%) and model evasions (21%). Incidents involving prompt injections and data poisonings made up 17% and 15% of cases, respectively.
Suja Viswesan, Vice President, Security and Runtime Products, IBM, commented: “The data shows that a gap between AI adoption and oversight already exists, and threat actors are starting to exploit it.”
She continued: “The report revealed a lack of basic access controls for AI systems, leaving highly sensitive data exposed, and models vulnerable to manipulation. As AI becomes more deeply embedded across business operations, AI security must be treated as foundational. The cost of inaction isn’t just financial, it’s the loss of trust, transparency and control.”
No tags.





































