The financial industry has been particularly affected by large-scale distributed denial-of-service (DDoS) attacks for years, but the recent escalating sophistication of these attacks marks a shift, according to the Financial Services Information Sharing and Analysis Center (FS-ISAC).
In a report published on June 10, in collaboration with Akamai, the financial sector’s threat intelligence sharing body revealed that the industry has experienced an almost exponential rise in DDoS attacks between 2014 and 2024.
From a residual amount of monthly volumetric DDoS attacks in 2014, the sector faced a peak of almost 350 events in October 2024 – with each event including hundreds, millions or billions of individual malicious requests.
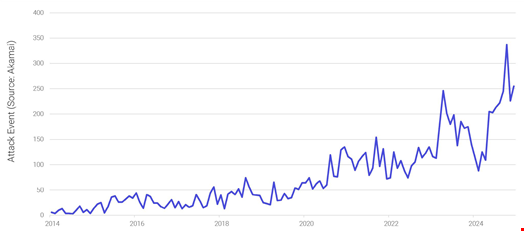 Volumetric DDoS attacks on financial services, 2014-2024. Source: Akamai, FS-ISAC
Volumetric DDoS attacks on financial services, 2014-2024. Source: Akamai, FS-ISAC
The report, titled From Nuisance to Strategic Threat: DDoS Attacks Against the Financial Sector, also showed that, after being the industry most targeted by DDoS attacks in 2023, the financial sector maintained its rank throughout 2024.
Moreover, the gap between DDoS attacks targeting financial businesses and other sectors, such as the gaming, manufacturing and high technology industries, significantly widened from April 2024, with financial services experiencing a stronger increase in such attacks than other sectors.
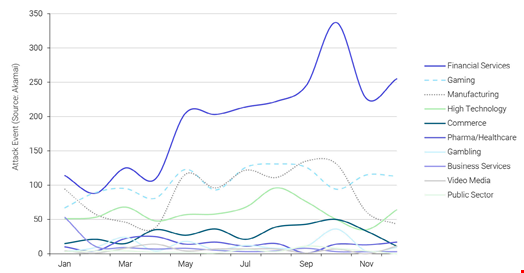 Volumetric DDoS attack trends by sector in 2024. Source: Akamai, FS-ISAC
Volumetric DDoS attack trends by sector in 2024. Source: Akamai, FS-ISAC
This dominance is partly explained by a 23% rise in application-layer DDoS attacks targeting financial services between 2023 and 2024.
According to Akamai’s telemetry, application DDoS attacks include:
- Web application attacks, which target user-facing components of web applications, such as login pages
- Attacks on application programming interfaces’ (APIs) features, such as login forms, payment gateways, or endpoints
Escalating Sophistication of DDoS Attacks
However, the report noted that the rise in scale of DDoS attacks is not sufficient to mark a fundamental shift. Even when large in volume, some basic DDoS attacks can be easily prevented or mitigated and only represent what the FS-ISAC and Akamai call a “nuisance” to the financial sector.
Specifically, what led the researchers to qualify DDoS attacks as becoming a “strategic threat” to financial businesses is that the rise in scale went hand-in-hand with increased sophistication, particularly since the last quarter of 2024.
“In 2024, threat actors increasingly employed advanced multi-vector DDoS strategies that incorporated systematic probing and adaptive tactics. This demonstrates an ability to analyze defenses in real time and dynamically adjust methods to evade automated protections,” noted the report’s authors.
Some of the observed advanced DDoS techniques included:
- DDoS defense mechanisms circumvention techniques, such as testing a wide range of attack vectors, often at low traffic volumes, to assess the effectiveness of different techniques
- Initial probing phase to gain intelligence, later used to deploy multi-vector DDoS attacks with significant traffic volumes, generally sustained over several weeks to months
- Bypassing automated DDoS defenses and disabling typical on-premise network (proxy, firewall, load-balancer) infrastructure
These sophisticated techniques suggest skilled, well-organized and motivated threat actors willing to invest time and effort to study their target’s infrastructure, the report noted.
“This marks a clear evolution in attacker capability, resources, and intent, and increases the threat of DDoS attacks against the financial services sector.”
Hacktivists Motivated by Rising Geopolitical Tensions
Some of the leading actors believed to be behind these advanced DDoS attacks include pro-Palestinian hacktivist groups BlackMeta (aka DarkMeta) and RipperSec as well as NoName057(16), one of the most active hacktivist groups that emerged in response to Russia’s invasion of Ukraine and the developer of the DDoSia tool.
Overall, the rise in scale and sophistication of DDoS attacks is fueled by increased geopolitical tensions, the report emphasized.
“While some DDoS attacks are launched by state-sponsored actors, geopolitical developments also inspire hacktivists. A notable example occurred in October 2024, when a DDoS campaign targeted multiple Australian financial institutions.”
The timing of this campaign, partly claimed by RipperSec, coincided with a series of significant geopolitical events, including the meeting of NATO Defense Ministers in Brussels, attended for the first time by officials from Australia, Japan, New Zealand, and South Korea, Australia's announcement of military aid to Ukraine and an address to the European Council by Ukrainian President Volodymyr Zelensky.
How to Mitigate Advanced DDoS Attacks
The Akamai and FS-ISAC report provided readers with a list of security measures that financial organizations can take to mitigate DDoS attacks, particularly the most advanced ones. These include:
- Geo-IP filtering, which can cut exposure by blocking traffic from regions where the firm has no business operation
- Dynamic traffic shaping to help manage attacks in real time, prioritizing critical services and shedding less important load when needed
- Infrastructure diversity and defense in depth approaches, which reduce reliance on a single vendor and add resilience against provider-targeted attacks
- Pre-agreed scrubbing support, which quickly triggers a response when thresholds or anomalies are detected
- An allowlisting security strategy – defining what is permitted and rejecting everything else – built into any implementation for network security and DDoS
- Threat intelligence fed directly into edge defenses to help block known malicious traffic before it causes disruption
- Regular DDoS playbook tests (e.g. red team activity, tabletop exercises) to ensure plans work under pressure
Finally, Akamai and the FS-ISAC also released a 5-level DDoS Maturity Model in the report, which financial institutions can use to assess their ability to withstand and respond to DDoS attacks.
No tags.


































