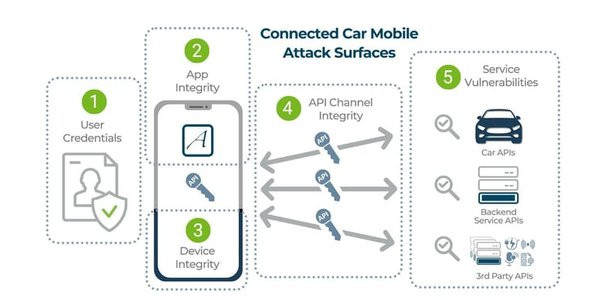
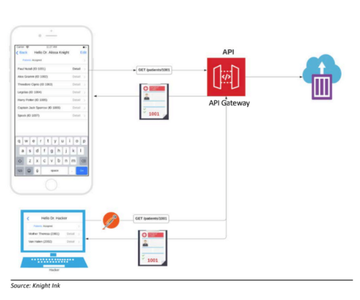
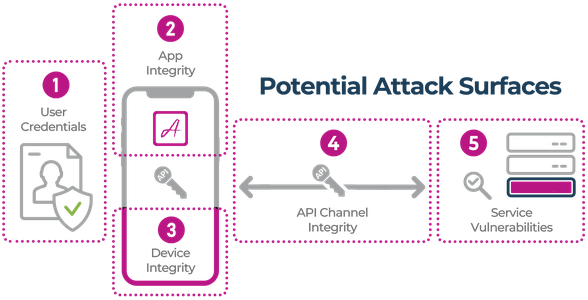
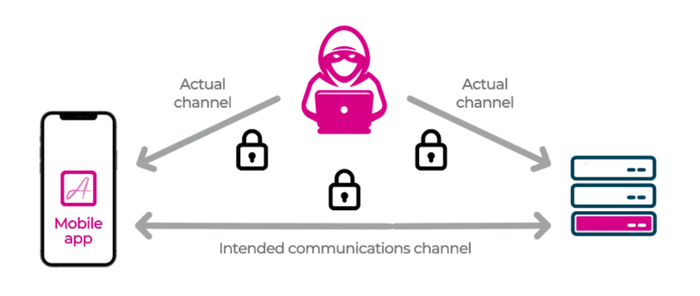
On-Demand Security Assessment:
Not sure if your game needs encryption? JikGuard provides free security testing and reports, helping you identify potential risks through penetration testing and in-depth analysis.
Minimal Performance Impact:
JikGuard’s encryption system only decrypts resources when needed, ensuring that files remain encrypted in the cache and have virtually no effect on loading speed or game smoothness.
Seamless Multi-Channel Packaging:
Supports mother package encryption, meaning all sub-packages remain protected without requiring additional processing for different distribution channels.
No SDK Required:
Unlike traditional solutions, JikGuard does not require SDK integration—simply run a command, and the encryption process is handled automatically.
Ultra-Low Performance Overhead:
▪ CPU usage increase: <0.2%
▪ Memory consumption: <1MB
▪ Startup time increase: <25ms
▪ Package size increase: <1.3MB
Ensuring a smooth and seamless gaming experience.
With JikGuard Game Protection, you can focus on game development while ensuring top-tier security against cheats, resource leaks, and competitive analysis. Protect your game today and keep your vision intact!