A hacker involved in the supply chain attack that targeted IT service provider Kaseya in July 2021 has claimed that he was coerced by the Russian government.
Yaroslav Vasinskyi, a former affiliate of the REvil ransomware syndicate known as ‘Rabotnik,’ serves a sentence of over 13 years in US federal prison at the Federal Correctional Institution, Danbury (FCI Danbury), Connecticut.
In a six-month conversation with Jon DiMaggio, chief security strategist at Analyst1 and author of the ‘Ransomware Diaries’ series, where he investigates the ransomware ecosystem, Vasinskyi revealed he tried to leave REvil several times for “moral” reasons but was blackmailed into preparing the Kaseya attack before leaving.
 Credit: T. Schneider / Shutterstock.com
Credit: T. Schneider / Shutterstock.com
Vasinskyi claimed REvil has ties with the Russian government and that the people who blackmailed him to keep conducting cyber-attacks were likely from Kremlin-linked government institutions.
DiMaggio unveiled his findings during a talk he gave alongside Trellix’s head of threat intelligence, John Fokker, at the DEFCON 33 event in Las Vegas on August 9.
The full written version of his investigation was published in the Ransomware Diaries Volume 7 report on August 9.
REvil Recruitment, Moral Crisis and Attempted Exit
Vasinskyi started working for REvil in early 2019 when he was “recruited” by a member of the group known as ‘Lalartu’ after finding a vulnerability in a ConnectWise server that was linked to around 1000 compromised PCs with various command-and-control (C2) functions.
He operated out of Poland, with a few trips to Ukraine while working with REvil.
During his email and phone conversations with DiMaggio, Vasinskyi claimed he attempted to leave REvil in March 2020 out of the belief that the deaths of this girlfriend's father and his grandmother were sanctioned against him for conducting cybercrime activities.
Additionally, Vasinskyi told DiMaggio that he “grew uneasy” and felt moral regrets after alleged REvil cyber-attacks against a Baptist church and a hospital, the latter reportedly led to a patient dying.
After asking REvil’s kingpin, an individual using the moniker UNKN, about this alleged death, Vasinskyi was told that although it was not an intended consequence, it ended up with “good publicity” for the ransomware gang.
While further investigation by DiMaggio seemed to indicate that the deadly cyber-attack against a hospital was likely conducted by Ryuk instead of REvil, “the casual dismissal of human death as good advertising’ disgusted Vasinskyi,” the security researcher wrote.
“It confirmed what he already feared, that the operation he had once rationalized as transactional had evolved into something colder, more detached, and more dangerous. Grieving, exhausted, and angry, Vasinskyi stepped away from REvil.”
Surveillance and Blackmail
However, Vasinskyi said his entire life was then under surveillance by some high-level institution.
When he travelled to Kyiv’s Boryspil airport in January 2021, he was stopped at passport control by customs, searched and driven out of the airport.
According to Vasinskyi, he was under pressure from someone connected to Ukrainian law enforcement who held leverage over him.
He later disclosed that one of these contacts was a powerful, high-ranking former intelligence officer. The blackmail, Vasinskyi claimed, was politically motivated, not financial.
The handler’s influence stretched far beyond Ukraine, hinting at either deep international intelligence ties or a sprawling cross-border corruption network.
“Vasinskyi’s worst fear had been confirmed. His ‘old friends’ leveraged their reach and power to create his legal troubles in Kyiv, and now they were using them to control him,” DiMaggio wrote.
What they wanted, Vasinskyi said, was for him to continue working with REvil. If he refused, they allegedly threatened to make sure he would go to jail, be tortured and even do harm to his girlfriend and family members.
Back in Poland, where Vasinskyi was based, the surveillance continued and his “handlers,” as he called the people pressuring him, were everywhere he went.
Kaseya, A Strategic Target
According to Vasinskyi, his “handlers” chose Kaseya as his next target “specifically for the cascading access its software provided, seeing an opportunity to inflict maximum damage through the company’s software distribution capabilities to thousands of downstream clients,” DiMaggio wrote.
Vasinskyi admitted to DiMaggio that he had entirely prepared the attack himself, from initial access to testing the final payload. However, he did not want to launch it himself and handed the payload delivery phase over to REvil.
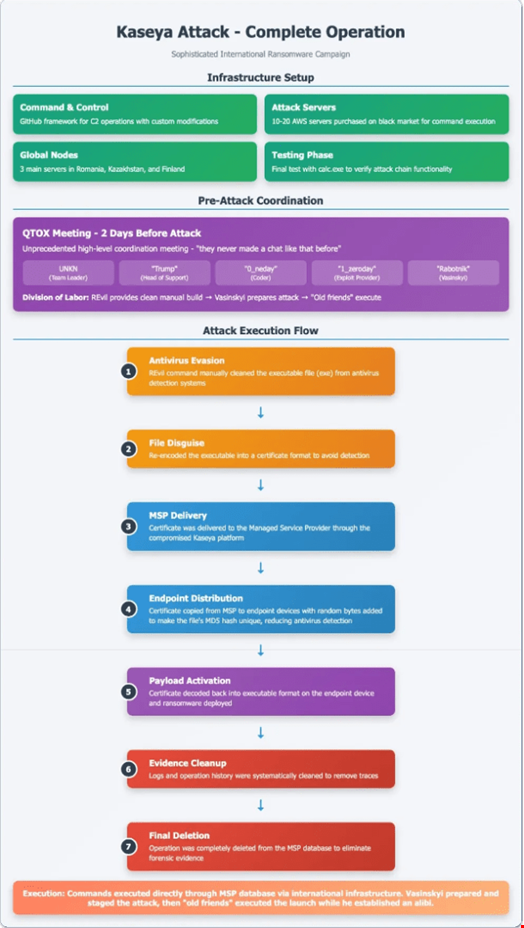 Vasinskyi’s alleged attack methodology was used in the Kaseya attack. Source: Analyst1
Vasinskyi’s alleged attack methodology was used in the Kaseya attack. Source: Analyst1
He also tried several ways to show that he did not execute the attack himself, including:
- Sending a letter to the FBI before the attack
- Using speakerphone during conversations with the REvil leadership team so that investigators potentially surveilling him could hear the conversations
- Showing his face to CCTV cameras while leaving Poland for Ukraine on the day the attack was executed
However, none of these pieces of evidence were used in Vasinskyi’s defence and he ultimately submitted a guilty plea.
UNKN, the persona behind which someone was running REvil, disappeared after the Kaseya attack, which compromised over 1500 companies across 17 countries and forced schools, pharmacies and entire supermarket chains offline.
Kaseya: Three-Tiered Operation with State-Level Handlers
While the Kaseya attack was attributed to REvil and a $70m ransom was demanded, Vasinskyi’s account suggests that the ransomware gang’s true role was strictly as a technical contractor, not an operational commander.
 UNKN taunting post on the day of the Kaseya attack. Source: Analyst1
UNKN taunting post on the day of the Kaseya attack. Source: Analyst1
According to Vasinskyi in DiMaggio’s reporting, REvil was only responsible for the build as an .exe file, nothing more, nothing less.
“They provided the weapon, but his handlers gave the order and pulled the trigger. This testimony lays out a three-tiered operational structure, separating REvil’s role as the ransomware provider from Vasinskyi’s as the technical lead tasked with preparing the attack and a third party, his state-level handlers, as the execution team,” DiMaggio explained.
“This wasn’t supposed to be about extortion. It was about disruption: crippling downstream systems, collecting intelligence, and gaining access to critical infrastructure,” the researcher added.
Additionally, Vasinskyi claimed that while REvil had connections to Russian government authorities, his own handlers were more powerful – operating at a level even the ransomware group couldn’t reach.
This suggested that his troubles stemmed not just from cybercriminal ties, but from entanglement with high-ranking figures whose influence eclipsed even that of REvil’s government-linked associates.
A theory on Russian cybercrime forums suggested that UNKN might have been Aleksandr Ermakov, a former Russian police officer arrested in July 2021 shortly after UNKN vanished. However, Vasinskyi disputed this, confirming Ermakov was part of REvil but not the only one associated to UNKN.
He believes that two people controlled the UNKN account: Ermakov, who took orders, and one who gave them. The true leader, Vasinskyi insisted, remained "Unknown."
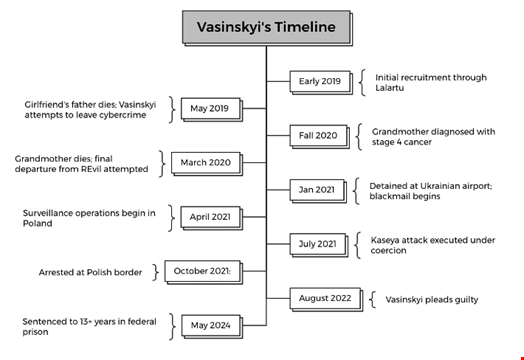 Vasinskyi's alleged timeline to the Kaseya Attack. Source: Analyst1
Vasinskyi's alleged timeline to the Kaseya Attack. Source: Analyst1
During his DEFCON talk, Analyst1’s DiMaggio highlighted that, while cybercriminals tend to lie a lot, Vasinskiy seemed to have never lied about things the researcher tested him on.
“At this point, he didn't have much to lose. There wasn't really a reason for him to lie to me. He's been sentenced to 13 years and seven months in prison, he's got $16m in restitution to pay and he has no chance of parole," conclude DiMaggio.
Photo credits: Felix Mizioznikov / mundissima / Shutterstock.com
Read more: Kaseya CISO on Preparing Effectively for the Next Cyber Incident
No tags.