Mobile App Security and API Keys
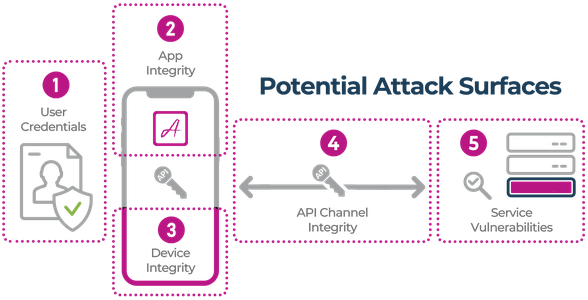
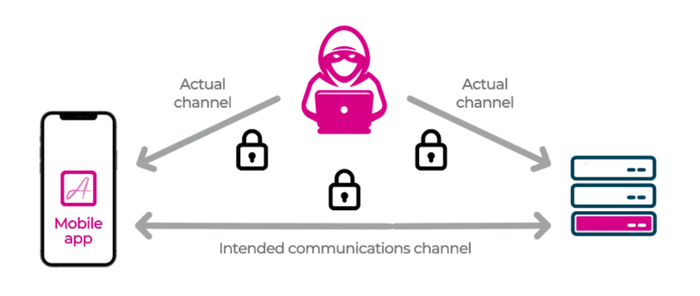
Secure mobile app operation is built on the requirement that only legitimate users without malicious intentions are accessing the service(s). Safety measures should ensure that they are using a genuine version of a mobile app, running on an uncompromised device, communicating directly with the API server via a secure channel and the API cannot be accessed by any other way. These are the “attack surfaces” targeted by bad actors.

A mobile app is a critical element of the overall application, accessing back-end elements to conveniently deliver the services. Both the mobile app code and the network environment it runs on are exposed and can be manipulated. Attacks can directly target mobile apps to steal data or can directly attack APIs using secrets acquired from mobile apps or elsewhere. Both types of vulnerabilities are commonly exploited. See below for a detailed description of five common mobile app attack surfaces.
API keys are commonly used to secure access to backend data based in the cloud. Typically, when apps use a third-party API, they sign up and get allocated a key. This identifies the app to the backend API and authenticates the app that’s making the call so the API backend knows which particular app is making the request. This blocks any anonymous traffic and can be used to limit data requests.
Tags:
No tags.