A Chinese-based threat actor has been observed using the flaws in Microsoft SharePoint to deploy ransomware on compromised systems.
In an incident update on July 23, Microsoft revealed that a group tracked as Storm-2603 is distributing Warlock ransomware on exploited SharePoint on-prem servers.
As a result, the tech giant has advised potentially affected organizations to expand their mitigation efforts to include protection against ransomware.
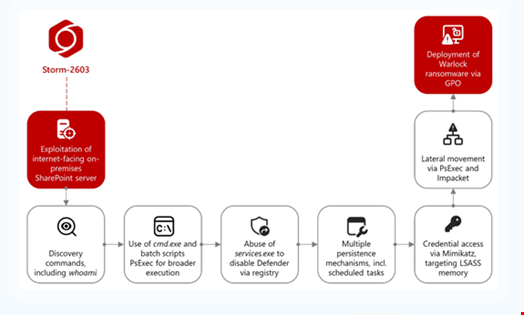 Storm-2603 attack chain exploiting SharePoint vulnerabilities and leading to ransomware. Source: Microsoft
Storm-2603 attack chain exploiting SharePoint vulnerabilities and leading to ransomware. Source: Microsoft
Storm-2603 is one of three groups observed to be exploiting on-prem SharePoint vulnerabilities, CVE-2025-53770 and CVE-2025-53771.
It has been assessed with moderate confidence that Storm-2603 is a China-based threat actor. The group has been known to deploy Warlock and LockBit ransomware.
Microsoft said it is currently unable to confidently assess the threat actor’s objectives.
The other two actors known to be exploiting the SharePoint vulnerabilities are Linen Typhoon and Violet Typhoon – two known Chinese nation-state groups primarily focused on collecting sensitive data from sectors such as government, defense, technology and human rights organizations.
The chained exploitation of the two bugs has been dubbed ‘ToolShell’ by the cybersecurity community. The attack chain appears to be sophisticated, with the threat actors bypassing identity controls and gaining privileged access in compromised systems.
Attackers Maximizing Impact
Kevin Robertson, CTO of Acumen Cyber, said the deployment of ransomware demonstrates that once inside a victim’s network, they will often look to take advantage in multiple ways.
“The attackers turning to ransomware are clearly taking advantage of CVE 2025-53770 to gain further access to environments, encrypting sensitive information, before executing ransomware hoping to get a big pay check,” he noted.
Chinese state-sponsored actors, not typically motivated by financial gain, could also be using the opportunity to deploy ransomware.
“They could be conducting reconnaissance on networks and then when they have what they need, dropping ransomware to cause further chaos for victims,” Robertson added.
SharePoint Victim Count Now Tops 400
Microsoft has told its on-prem SharePoint customers to assume compromise, even if they have fully patched the two vulnerabilities.
Organizations have been advised to urgently take mitigations such as rotating cryptographic material, engaging professional incident response and even disconnecting SharePoint from the internet.
Cybersecurity vendor Eye Security reported on July 23 that over 400 SharePoint systems have been actively compromised so far.
These exploits took place over four confirmed waves of attack on July 17, 18, 19 and 21.
Multiple waves took place on and after July 21 following a public proof-of-concept CVE-2025-53770/CVE-2025-53771 exploit script was released on GitHub, Eye Security added.
It has been reported that several high-profile US government agencies are among the victims of the SharePoint campaign.
Bloomberg reported on July 23 that on-prem SharePoint servers used by the National Nuclear Security Administration and the Department of Education were compromised, while the Washington Post reported that the Department of Health and Human Services (DHHS) had been hit.
NextGov said that it had been informed by people familiar with the matter that the Department of Homeland Security (DHS) was also among the victims of the Chinese hackers.
No tags.








































