Threat actors are becoming faster at exploiting vulnerabilities and rely more than ever on zero-day exploitation.
According to VulnCheck’s latest report which covered the first half of 2025, almost one-third (32.1%) of vulnerabilities listed in the vulnerability intelligence provider’s Known Exploited Vulnerabilities (KEV) catalog were weaponized either before being detected or within 24 hours of disclosure.
This represents an 8.5% increase from 23.6% in 2024.
In total, VulnCheck added 432 new vulnerabilities in its KEV list in the first half of 2025.
This is already more than half of the 768 Common Vulnerabilities and Exposures (CVEs) that were publicly reported as exploited in VulnCheck’s telemetry in 2024.
Microsoft and Cisco, Top Targeted Vendors
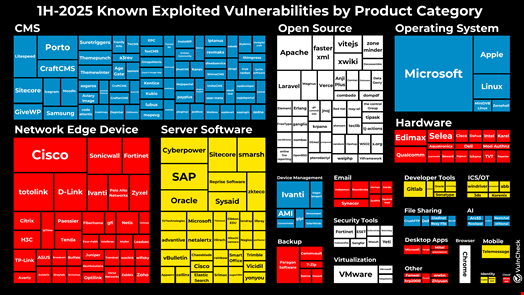
The top categories of vulnerabilities in VulnCheck’s KEV list for the first half of 2025 include:
- Content management systems (CMS) at 86, with a dominance of WordPress plugin vulnerabilities
- Network edge devices at 77, with Cisco, Fortinet, SonicWall, D-Link and Ivanti among the top targeted vendors
- Server software at 61, with Cyberpower, SAP, Oracle and Sitecore among the top targeted vendors
- Open-source software at 55
- Operating systems (OS) at 38, with a dominance of Microsoft, followed by Apple and Linux
Microsoft was the most targeted vendor overall, with 32 CVEs appearing in VulnCheck’s KEV list for the reported period, followed by Cisco with 10 CVEs.
 Source: VulnCheck
Source: VulnCheck
The ‘Hardware’ category experienced a notable increase in KEVs as VulnCheck issued CVEs for several vulnerabilities targeting camera systems, DVRs and IP phones, among other hardware devices, where exploitation evidence had been identified by the Shadowserver Foundation, a UK-based non-profit and the most active contributor of KEV reporting.
Chinese and North Korean Threat Actors Down, Russians and Iranians Up
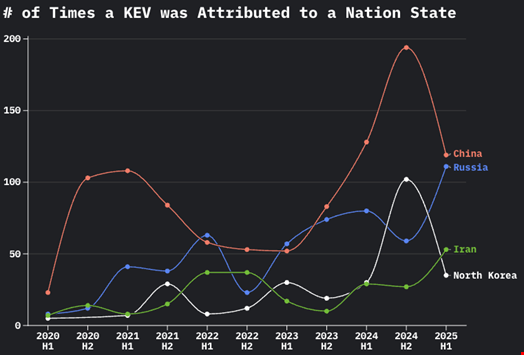
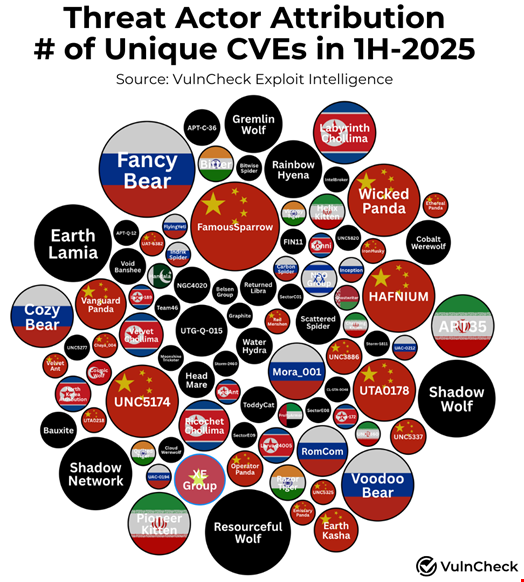
During the reported period, VulnCheck identified 92 unique threat actors, with 56 (60.8%) attributed to specific countries. The most active state-linked groups exploiting known vulnerabilities originated from China (20), Russia (11), North Korea (9) and Iran (6).
However, VulnCheck observed notable shifts in exploitation patterns. While still dominant, Chinese threat actors saw a decline in reported KEVs, with attributions dropping from nearly 200 in the second half of 2024 to just over 120 in the first half of 2025.
Similarly, North Korean actors experienced a sharp decrease, with KEV attributions falling from over 100 in the previous period to fewer than 40 in the first half of 2025.
 Source: VulnCheck
Source: VulnCheck
In contrast, Russian and Iranian threat actors increased their exploitation efforts. Russian groups nearly doubled their activity, rising from just over 50 KEVs in the second half of 2024 to almost 120 in the first half of 2025.
Meanwhile, Iranian actors surpassed North Korea in KEV exploitation, with attributions climbing from approximately 25 in the second half of 2024 to more than 50 in the first half of 2025.
Finally, 147 of 181 unique CVEs that were used by known threat actors had evidence of exploitation before 2025, demonstrating that threat actor exploitation disclosure often continues long after the disclosure of initial exploitation evidence.
 Source: VulnCheck
Source: VulnCheck
Read now: CISA Urged to Enrich KEV Catalog with More Contextual Data
No tags.






































