Although the open source ecosystem has brought Android better development space, it has also brought with it a lower threshold for hacking and more serious security issues. A common method of cheating in Android games is to obtain root privileges to provide an environment for game cheats and hacks.

Magisk is a common root tool on the market, whose main features are to provide root permissions for devices and to hide root and itself. The root permissions provided by Magisk can provide the necessary environment for memory modification, speed changes, and other cheats, while the hiding feature makes it difficult for games to detect cheating.
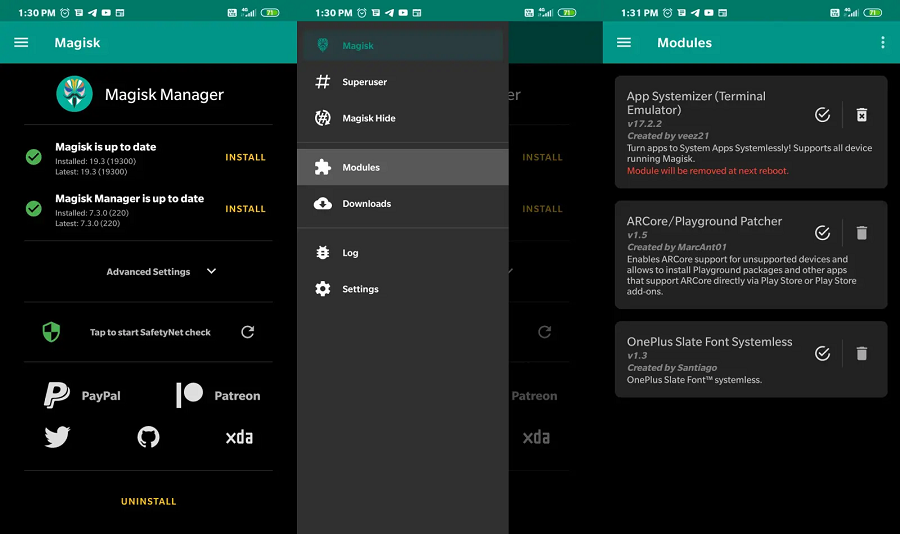
Magisk interface
Although the Magisk Hide feature has been removed in the current version, Magisk can still be hidden through other means, such as the new feature ‘Zygisk’.
Zygisk hooks the Android core process Zygote and injects Magisk's code when the application is launched. In this way, Magisk can provide root permissions while the application is running, without the need to enable root globally when the system starts up. This prevents conventional game security detection from recognising the existence of root permissions and Magisk.
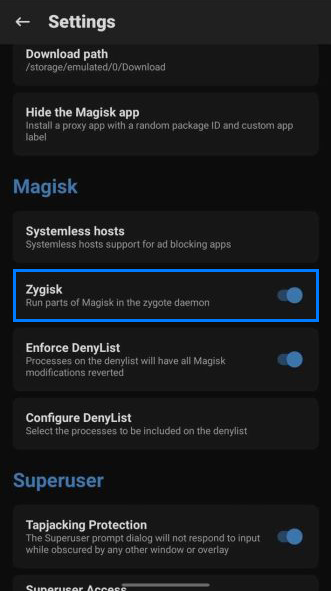
Hiding features Zygisk
In addition, Magisk can also use randomised package names, edit new application names, and reinstall to prevent detection. After repeatedly hiding Magisk application operations, the package names and signatures of different installations can also be randomised.
In response to the Magisk cheating problem faced by games, JikGuard has customised an exclusive solution, which has been integrated into many popular games and has proven its excellent detection capabilities.