The booming mobile gaming market has attracted profit-seeking Game Black/Gray Industries, with numerous games facing varying degrees of security threats. Common issues include memory modification, auto click, injection, and other Cheats, as well as more severe “Hack” tactics.
Hacking refers to the process where hackers use tools to bypass a game's signature verification, perform reverse engineering and debugging on its internal code logic, modify game values and logic, and implant feature menus, thereby creating a hacked version of the game.
Direct-install hacks are modified versions that bypass login verification. These hacked versions allow instant gameplay upon download, making them highly appealing to cheaters while posing a more severe threat to the game.
This paper will analyze the principles behind direct-install hacks in mobile games through case studies and provide targeted detection solutions.
Creating hacked versions of games typically involves reverse engineering tools such as MT Manager. After obtaining root privileges, these tools allow access to system directories, mount file systems for read/write operations, and modify file permissions and ownership.
Its primary functions include: signature verification removal, APK editing, DEX editing, XML editing, APK signing, and RES resource deobfuscation.
After bypassing signature verification, hackers decompile the game's code logic and tamper with memory values and game mechanics to implement various Cheats. They also implant menu modules to facilitate operations.
Finally, Hack developers perform secondary repackaging on the hacked version. They embed the genuine package within the hacked package, utilizing hooking frameworks or techniques like IO redirection and system API overwriting to hijack the call targets of detection code to the genuine package nested within the hacked package.
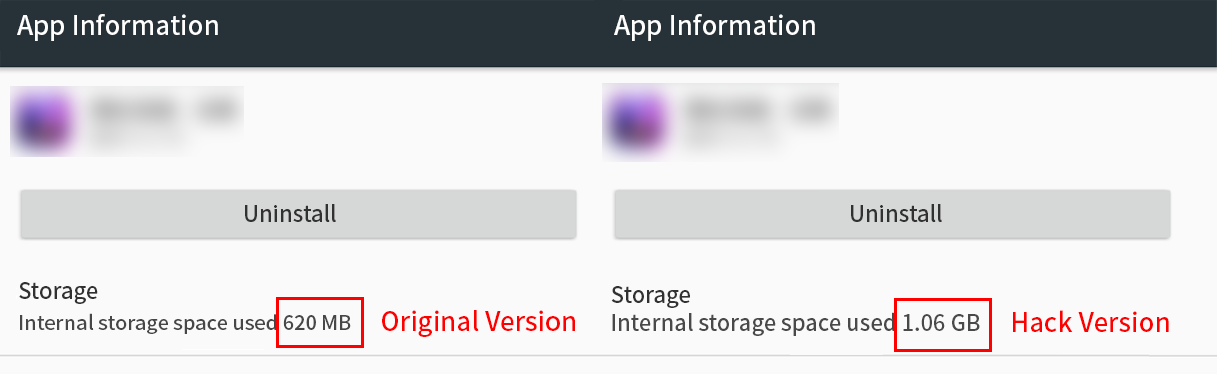
In this way, when the game launches and performs signature verification, it obtains the genuine signature, while the actual content running during gameplay is from the Hacked package. This discrepancy is often reflected in the package size, with Hacked versions typically being nearly twice as large as their legitimate counterparts.
In addition to the aforementioned methods, we have also observed instances where the designing tool SRPatch is used to bypass signature verification.
SRPatch is an APK unsignature tool specifically designed for the Android platform. It bypasses original signature verification restrictions with a single click and supports multiple unsignature solutions, enabling secondary modification, debugging and testing, as well as efficient repackaging of APKs.
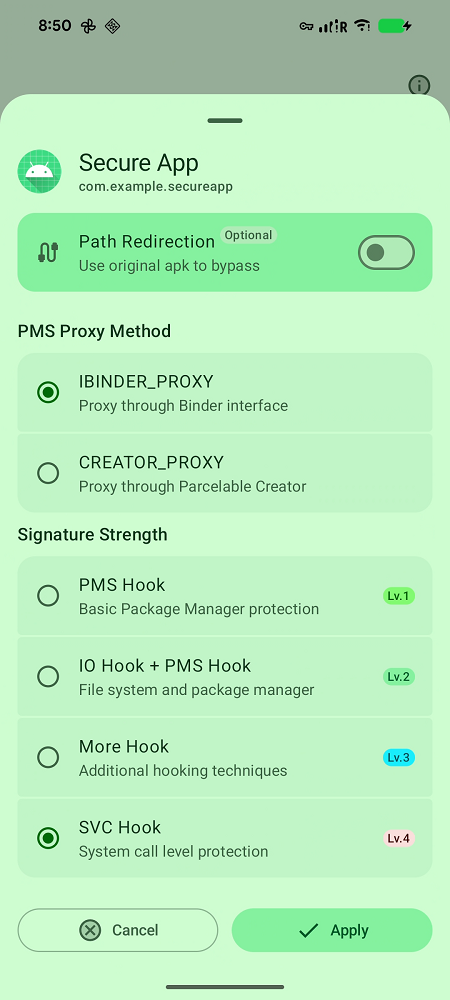
Taking the PMS Hook feature as an example, SRPatch deletes or empties the signature core files within the META-INF directory of the APK, directly compromising the data source for the system's static signature verification. It then hooks the PMS process to modify its execution logic, thereby causing the system to bypass the APK signature validity check.
Compared to cheats, pirated versions inflict far more severe damage on games. Pirated direct-install hacks often come bundled with a series of extreme modifications that drastically disrupt game balance, leading to massive player attrition among legitimate users and significant revenue losses for developers. Furthermore, there is a risk that in-game code and art assets may be stolen or spoiled.
To address the risk of direct-install hacks in games, JikGuard has developed a specialized countermeasure. This solution has been integrated into multiple popular games and has demonstrated outstanding protection capabilities.
Anti-Hack Features
JikGuard's industry-exclusive “API Signature Verification-Free Technology” employs deep encryption on game engines and code, coupled with multi-layered verification of game package signatures and file integrity. This significantly reduces the possibility of bypassing security measures, preventing malicious modules from being implanted into games or advertisements from being stripped out.
Proactive Malicious Module Detection Mechanism
Unlike other security products on the market that require obtaining samples before combating Cheats, JikGuard's exclusive “Proactive Malicious Module Detection Mechanism” actively identifies suspicious modules within games. Combined with its online countermeasure capabilities, this enables proactive defense, significantly reducing the time required to investigate and eliminate Cheats.
Anti-Debugging Feature
Prevents Cheats developers from debugging the game and blocks static or dynamic analysis. Upon detection, the game will immediately crash.
Security Environment Detection Capabilities
Unlike other products on the market, JikGuard employs deeper-level detection methods to accurately identify various risk environments such as virtual frameworks, virtual machines, jailbreaks, root access, and cloud phones, while providing customized crash prevention strategies.







