Unit 42, the research team at Palo Alto Networks, has identified a new malicious campaign targeting many financial organizations across Africa.
The attackers, tracked as CL-CRI-1014, have been actively targeting the African financial sector since at least 2023. The Unit 42 researchers assessed that they act as initial access brokers (IABs), gaining initial access to their targets and then selling it to others on the dark web.
To deploy their attacks, the hackers typically leverage a set of open-source tools, including PoshC2, an attack framework, Chisel, a tunneling utility, as well as publicly available software like Microsoft’s PsExec and Classroom Spy, a remote administration tool. The latter replaced MeshAgent, which was used in CL-CRI-1014’s previous campaigns.
They also create tunnels for network communication and perform remote administration.
The Unit 42 findings were shared in a report published on June 24.
Attack Chain Explained
Here is a breakdown of the typical attack chain performed in CL-CRI-1014’s latest campaign as observed by the Unit 42 researchers:
- The threat actor uses PsExec to connect to another machine remotely, used as a proxy
- Chisel is used on the proxy machine to bypass firewall protections in the system of the target organization and connect to several machines
- On some machines, the threat actor uses PsExec to deliver PoshC2 and perform reconnaissance across the system, tunnelling the network traffic via Chisel
- On other machines, the threat actor uses PsExec to run PowerShell and install Classroom Spy
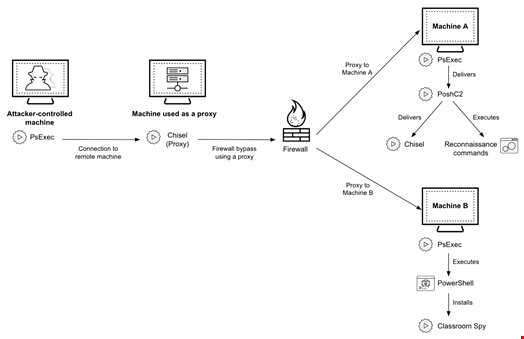 How the threat actor used PsExec, Chisel, PoshC2 and Classroom Spy as part of their attack playbook. Source: Unit 42, Palo Alto Networks
How the threat actor used PsExec, Chisel, PoshC2 and Classroom Spy as part of their attack playbook. Source: Unit 42, Palo Alto Networks
PoshC2 was a key tool the attackers used to execute commands and gain a foothold in compromised environments. The PoshC2 framework supports generating different implant types (PowerShell, C#.NET and Python) and comes preloaded with various attack modules.
Classroom Spy comes with a range of features, including the following:
- Live monitoring of the computer screen (including taking screenshots)
- Controlling the mouse and keyboard
- Collecting and deploying files to and from machines
- Logging visited webpages
- Keylogging
- Recording audio
- Accessing the camera
- Opening a terminal
- Collecting system information
- Monitoring and blocking applications
Finally, CL-CRI-1014 employed various methods to evade detection, including using packers, signing its tools with stolen signatures and using icons from legitimate products.
There is no evidence that the campaign exploited any vulnerabilities in the target organizations’ products or services.
No tags.